How to Protect Your Business from Virus, Malware and Ransomware Attack. These days, there are so many reports of breaches, hacks and attacks. Your business is ever more reliant on the key security controls you have in place and it’s critical to review these areas to make sure they are doing the job they need to and fit for purpose.
Over the last few years, the methods criminals use are more diverse and well thought out. Any targeted attack may not start with a blanket email asking someone to click a link and enter their credentials, it’s more likely to be well structured, identifying the right target employees in the business, and a number of methods tried to get access to your systems and data.
It’s important to understand some of the key threats, and in this short blog, we talk about the differences between the three main types of threats, rather than their delivery method.
Protecting Your Business from Malware
This is an all-encompassing term for any software that is designed to run on your computer, for example, and try and gain access or be as destructive as possible. Quite often it’s. used to get elevated privileges on the computer in order to traverse your network or gain access to the data you have in the business.
These can be delivered in a number of ways, from a USB stick found in a car park by a curious employee (yes, it happens) through to a targeted phishing attack tricking an employee into clicking a link and covertly downloading a small piece of malware to do with what the criminal needs.
The threats by malware are wide-ranging. From the more severe around Ransomware, through to applications designed to kill processes on your computer or slow it down, or totally incapacitate the computer.
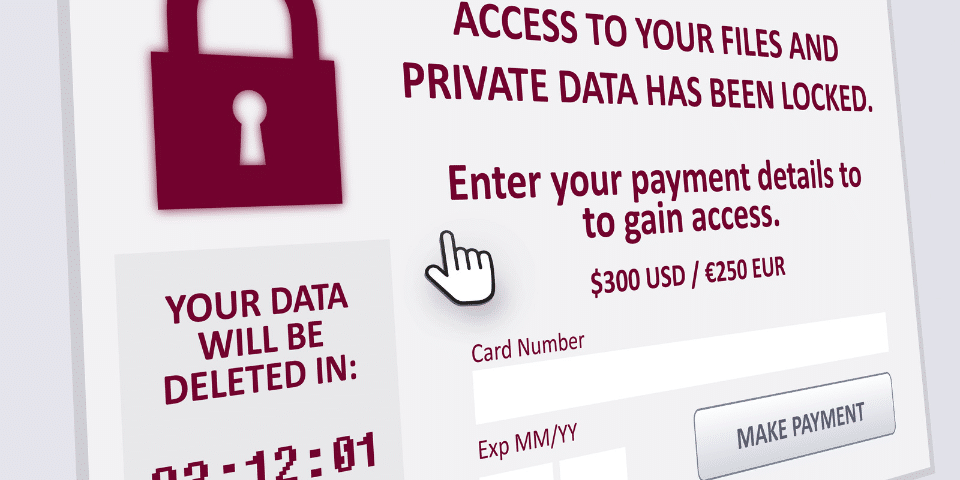
Ransomware and Keeping Your Business Secure
This is a subset of the all-encompassing Malware. Any form of Ransomware is severe, and once its on your computer, it can be hard to recover your data.
Ransomware is designed to have the maximum effect. And it always used to be that the application ran, encrypted your data and then a link was displayed for you to pay in the hope you got your data back. These days, as we have written about before, Ransomware is designed to extract the data from your business first, then threaten if you don’t pay, we will release that data.
In the latter case, your business is caught between a rock and a hard place, The advice is never to pay any criminal activity, but when your business is faced with no backups and the need for that encrypted data, or even worse, the threat of releasing your customer’s personal information out to the highest bidder – what would your business do? It’s a tough choice on protecting your business against this type of virus attack.
Even if you do pay, and it’s usually negotiated in a public forum open to everyone, there is no guarantee that the threat actor will follow through on their promises and either not release that data or destroy it completely. What’s stopping them from coming back and asking for more money – where does it stop?
Viruses
This is another Malware type ( others include Spyware, Greyware etc ) and although the term is generic, generally speaking, viruses is software that is designed to spread quickly and effectively across your network infrastructure. Normally they are designed to spread efficiently, cause maximum impact and exploit specific vulnerabilities in the business.
These days they are designed to bypass critical security controls – they can be designed to wait for the exploit, in order to bypass sandbox AV detection, and work in such a way that they mimic user behaviour. They can even be delayed to action, in some cases for up to a year before the malware becomes active.
How to Protect your Business from a Virus Attack
Deploy a fantastic Malware protection solution. This should be the last line of defence ideally. Make sure it’s a solid service, recommended and has an EDR capability. EDR is all about enhanced detection and looking for a behavioural activity for the Malware.
User education – keep your users up to date with the latest threats and information out there when it comes to malware, ransomware and attacks. Make sure they know what to look out for when they receive an email to make sure it’s valid and they aren’t inadvertently being tricked into clicking a link
Dark Web – keep a close eye on the Dark Web, make sure your business accounts and data isn’t being discussed or bought/sold on the Dark Web.